We guarantee to have a technician working on a problem within 60 minutes or less of your call. This is written into every service agreement we give to our clients because it’s standard procedure.
HOW NEXT I.T. CAME TO BE...
HI, MY NAME IS ERIC RINGELBERG
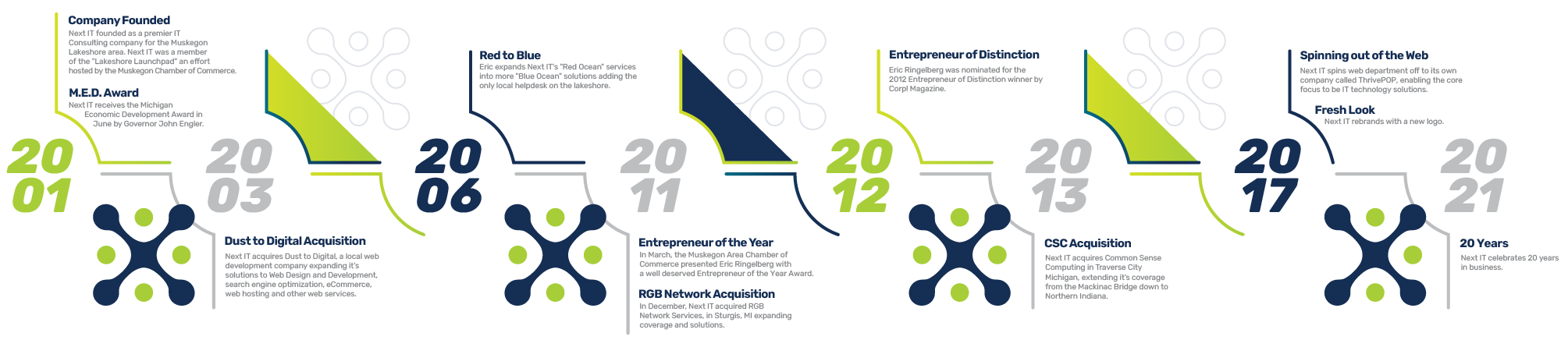
I started Next I.T. in 2001 in the basement of my home. With a lot of hard work, the right people, and a little luck we have grown to 3 offices across Michigan. Our clients range from manufacturers to schools, government, wineries, etc… They all want the same thing – to reduce risk, be more productive, and leverage their technology so their organizations can grow!
Next I.T. delivers industry-specific technology solutions that are secure, scalable, and reliable. Our proven I.T. solutions are built with industry best practices and provide a strategic advantage in today’s competitive environment.
We are proud to be a local, award-winning, Managed I.T. Computer Support provider. We have been recognized by many of the top technology manufacturers as a partner; Cisco Premier Certified Partner, Microsoft Silver Certified Partner, VMware Enterprise Partner, VEEAM, HP, WebRoot, Lenovo, DELL, and many more.
Next I.T. is different from our competitors because we focus on technology solutions that make business sense for YOU. Our size and independent ownership make Next I.T. the ideal technology partner for most small and mid-size organizations. We are large enough to maintain close relationships and purchasing leverage with all major suppliers, yet not so big that we forget how important your business is to our business.
Thank you for considering us!
Best Regards,
Eric Ringelberg
WHY SO MANY BUSINESSES DEPEND ON
NEXT I.T. FOR SERVICE & SUPPORT
MANAGED
I.T. Services
- Unlimited On-Site & Remote Support
- Dedicated Technical Alignment Manager
- Quarterly Business Technology Reviews
- I.T. Budgeting and Strategy
- Asset Lifecycle & Warranty Management
- Pro-Active Server & Infrastructure Management
- Vendor Management
- Licensing Management
MANAGED
Back-Up Solutions
- Image Level Server Backups
- Office 36S Email & OneDrive Backups
- On-Site / Offsite Backup Solutions
- Quarterly Backup Test Restores
- Disaster Recovery Management
MANAGED
Security
- Intelligent Security Monitoring & Alerts
- Managed Cyber Threat Detection & Response
- Managed Multi-Factor Authentication
- Password Management & Protection
- Ransomware protection
- Mobile Device Management
- End user Security Awareness Training
- Advanced Threat Protection
- Anti-Virus / Anti-Spam Protection
- Web Content Filtering
- DNS Layer Internet Security
- Dark Web Breach Assessments
- Email Phishing Campaign Management
THE UNIQUE SOLUTIONS FOR YOUR BUSINESS
Satisfied
Successful IT Projects
Company Offices
in Michigan
16 Questions You Must Ask Before Hiring Any I.T. Company
-
Do you have a written, guaranteed response time to your calls?
-
Do they provide detailed invoices that clearly explain what you are paying for?
We provide detailed invoices that show what work was done, why and when, so you never have to guess what you are paying for. We also double-check our invoices for accuracy before they are sent to you.
-
Do they take the time to explain what they are doing and answer your questions in terms that you can understand (not geek-speak), or do they come across as arrogant and make you feel stupid for asking simple questions?
Our technicians are trained to have the “heart of a teacher” and will take time to answer your questions and explain everything in simple terms.
-
Do they consistently (and proactively) offer new ways to improve your network’s performance, or do they wait until you have a problem to make recommendations?
We conduct quarterly review meetings with our clients to look for new ways to help improve their operations, lower costs, increase efficiencies and resolve any problems that may be arising. Our goal with these meetings is to help our clients be more profitable, efficient and competitive.
-
Do they insist on remotely monitoring your network 24-7-365 to keep critical security settings, virus definitions and security patches up-to-date and PREVENT problems from turning into downtime, viruses, lost data and other issues?
Yes, our remote network monitoring system watches over your network to constantly look for developing problems, security issues and other problems so we can address them BEFORE they turn into bigger problems.
-
Do they guarantee to complete projects on time and on budget?
All projects are fixed-priced and guaranteed to be completed on time, in writing. This is important because many unethical or incompetent computer guys will only quote “time and materials,” which gives them free rein to nickel-and-dime you as well as take as much time as they want on completing a project.
-
Do they have adequate errors and omissions insurance as well as workers’ compensation insurance to protect YOU?
Here’s something to consider: if THEY cause a problem with your network that causes you to be down for hours or days or to lose data, who’s responsible? Here’s another question to consider: if one of their technicians gets hurt at your office, who’s paying? In this litigious society we live in, you better make darn sure whomever you hire is adequately insured with both errors and omissions insurance AND workers’ compensation – and don’t be shy about asking to see their latest insurance policies!
-
Do they take the time to explain what they are doing and answer your questions in terms that you can understand (not geek-speak), or do they come across as arrogant and make you feel stupid for asking simple questions?
We guarantee to have a technician working on a problem within 60 minutes or less of your call. This is written into every service agreement we give to our clients because it’s standard procedure.
-
Do they provide you with a weekly report that shows all the updates, security patches and the status of every machine on your network so you know for SURE your systems have been secured and updated?
Every week our clients get a detailed report that shows an overall health score of their network and the updates to their antivirus, security settings, patches and other important network checks (like hard-drive space, backups, speed and performance, etc.).
-
Is it standard procedure for them to provide you with written network documentation detailing what software licenses you own, critical passwords, user information, hardware inventory, etc., or are they the only person with the “keys to the kingdom”?
All clients receive this in written and electronic form at no additional cost. We also perform a quarterly update on this material and make sure certain key people from your organization have this information and know how to use it, giving you complete control over your network.
Side note: You should NEVER allow an IT person to have that much control over you and your company. If you get the sneaking suspicion that your current IT person is keeping this under their control as a means of job security, get rid of them (and we can help to make sure you don’t suffer ANY ill effects). This is downright unethical and dangerous to your organization, so don’t tolerate it!

